Cybersecurity in the Age of IoT: Risks and Best Practices
In the age of IoT, where devices seamlessly communicate and integrate into our daily lives, cybersecurity has become more crucial than ever.
The Internet of Things (IoT) devoid of comprehensive security management is tantamount to the Internet of Threats. Apply open collaborative innovation, systems thinking & zero-trust security models to design IoT ecosystems that generate and capture value in value chains of the Internet of Things.
Stephane Nappo, Chief Information Security Officer
Discover the World of IoT Cybersecurity
The Internet of Things (IoT) links different items and machines together so they can talk with other similarly connected machines or gadgets. Consumers can now buy a variety of things, from cars to refrigerators, using an online connection. We may become more effective, save time and money, and have access to our digital lives whenever we need it by expanding networking capabilities to every part of our lives.
Need for Security in IoT
IoT device security is extremely difficult to achieve for a variety of reasons. Time-to-market is frequently given precedence over effective security measures by manufacturers in their rush to introduce innovative products. In addition, many companies continue to be blind to the security flaws in IoT, concentrating instead on the cost savings and convenience it provides. According to alarming Gartner forecasts, IoT will be responsible for more than 25% of enterprise intrusions by 2020. The stakes are especially high in industrial IoT (IIoT) systems, where connected sensors and devices increase operational hazards and have an effect on crucial infrastructures like global manufacturing processes and national power grids.
In addition to securing individual IoT devices, organizations must prioritize the security of their IoT networks. Strong user authentication and access control mechanisms are essential to ensure that only authorized users can access the IoT framework. However, despite the significant advantages that the Internet of Things offers to businesses, the proliferation of IoT devices and the complexity of the IoT ecosystem contribute to an increased number of security vulnerabilities, spanning from edge devices to cloud platforms. Regrettably, many businesses continue to delay implementing comprehensive IoT cybersecurity strategies and fail to recognize the gravity of IoT security risks until they suffer the consequences of a breach.
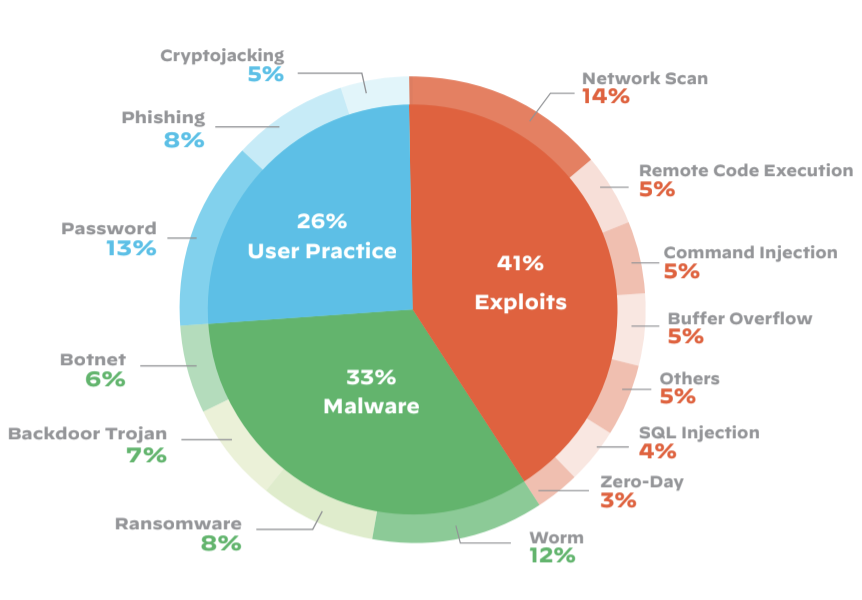
Unveiling the Unseen: Common Risks in the Interconnected Web of IoT
98 percent of IoT device traffic is unencrypted, meaning it’s in the clear, anyone can go and see it if they can access it on that network sort of gives you an indication of how the software and how the protocols for these are being done. Below are the areas of attacks related to certain fields.
some common risks connected to the Internet of Things and discuss how they can impact individuals, businesses, and society as a whole.
Security Breaches and Data Privacy
Security breaches are one of the main issues with IoT. Unauthorized access and data breaches are more likely as more devices are connected. Cybercriminals may gain access to sensitive information due to a lack of security measures, unpatched vulnerabilities, and lack of encryption. Identity theft, unauthorized surveillance, and the compromise of personal or financial data can result from this. These dangers can be reduced by securing IoT devices with strong passwords, frequent upgrades, and encryption protocols.
Our Readers ALSO READ
Artificial Intelligence and Cybersecurity: Opportunities and Risks
Device Vulnerabilities and Exploits:
IoT devices are particularly vulnerable to assaults since they frequently have low processing and memory capacity. These weaknesses can be used by hackers to take control of the equipment and use it as a gateway into larger networks. Infiltrating critical infrastructure systems or launching distributed denial-of-service (DDoS) assaults are all possible with compromised IoT devices. Such attacks can be prevented with frequent firmware updates, network segmentation, and network monitoring.
Lack of Standardized Security Measures
Due to the variety of devices from various manufacturers that make up the IoT ecosystem, there are no standardized security procedures in place. It is difficult to build standardized security methods and best practices because of this variety. Furthermore, outdated hardware can not get fixes or updates, leaving it open to attacks. To build strong security standards and guarantee the safety of IoT devices, cooperation between manufacturers, governing bodies, and industry standards organizations is essential.
Privacy Concerns and Data Collection
IoT devices gather a ton of information about user routines, preferences, and behavior. Although this data can provide customized interactions and effective automation, it also creates privacy issues. Unauthorized access to or misuse of this data may result in user behavior manipulation, targeted advertising, or even profiling. To address these privacy threats and guarantee users have control over their personal information, it is vital to implement clear consent methods, open data-gathering procedures, and robust data protection laws.
Physical Safety Risks
IoT devices are being employed more frequently in industrial settings, critical infrastructure systems, and healthcare applications. For human safety, any breach or malfunction of these technologies could have serious repercussions. For instance, a vulnerable linked automobile could cause accidents while a hacked medical IoT equipment could endanger the health of patients. To reduce the dangers to physical safety connected with IoT deployments, rigorous testing, adherence to safety standards, and routine maintenance are essential.
Exploring the Lucrative IoT Security Market
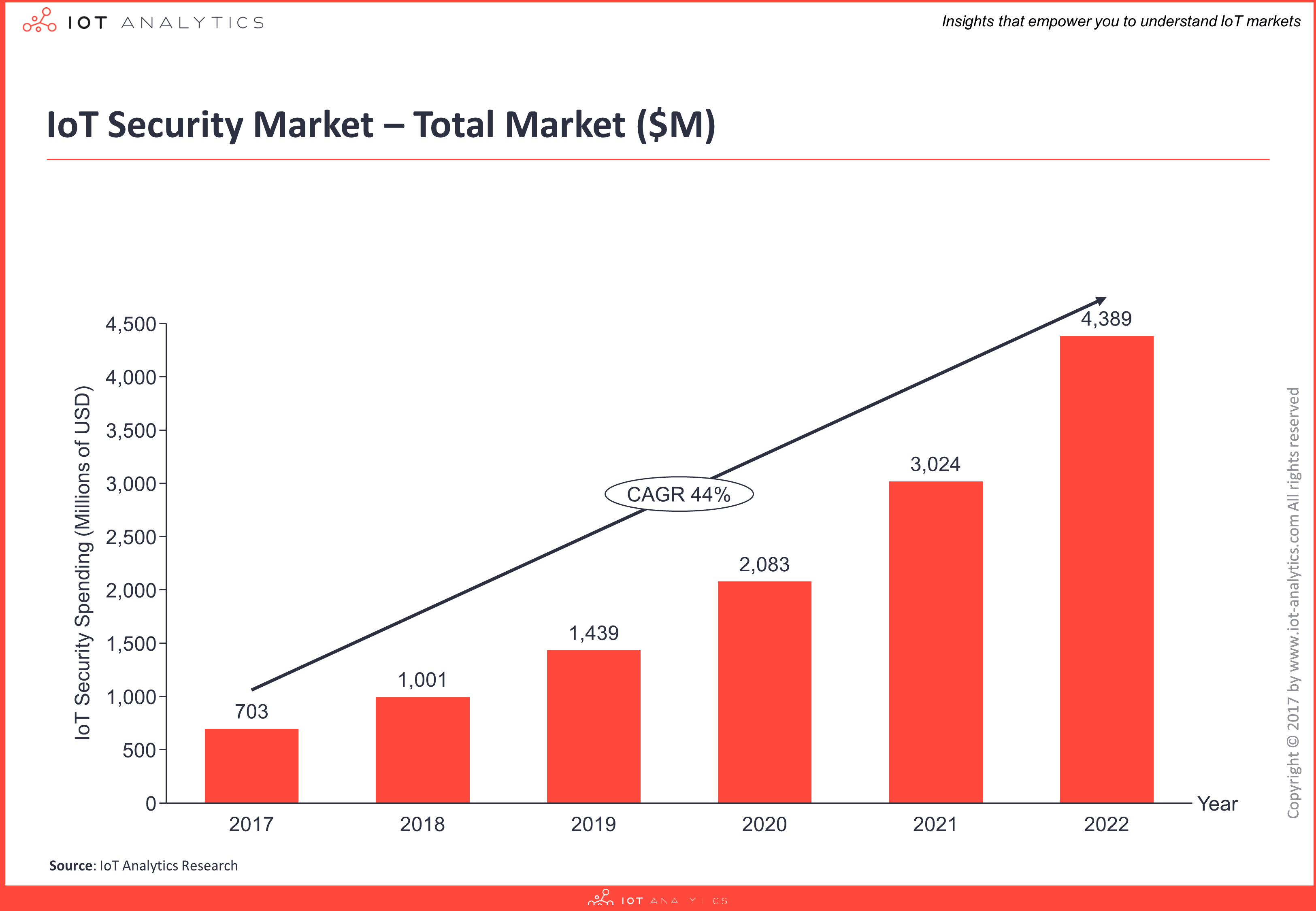
The current estimated global spending on IoT security is $703M for 2017, and it is anticipated to increase at a CAGR of 44% over the following six years, creating a market opportunity of $4.4B by 2022 (forecasts are based on the IoT security-related revenue of leading technology companies operating across 12 industries and 21 technology areas).
The worldwide semiconductor industry, infrastructure suppliers, cloud and enterprise software providers, as well as creative startups and well-established businesses make up the IoT security market.
With an estimated 7% market share, Cisco is now the industry leader in the fragmented IoT security market. Over 40% of the market for IoT security is accounted for by the top 10 providers.
Best Practices for IoT in Cybersecurity
Modify passwords: The most vital advice is this. After configuring IoT devices, do not use the default login and password! Change them to something safe and difficult to guess every time.
Think about setting up a VPN on your router: Despite being placed on routers, VPNs are more frequently utilized on desktops. By encrypting data and masking IP addresses, your router will safeguard all devices connected to it when you equip it with a VPN. Additionally, you can access content that could be prohibited in your area by utilizing a VPN for Australia or any other nation.
Securing the Network: Speaking of routers, even if you have a VPN set up, be sure your network is safe. Change the default passwords and SSIDs, use encryption, and enable firewalls and MAC filtering if possible.
Update: Devices or software that are out of date are the cause of many security breaches. Don’t wait indefinitely to install updates if there are any available. Security flaws are frequently exploited by hackers, thus patches are made to close them up before bad things happen.
The Internet of Things is designed to empower individuals, but unfortunately, with every technological advancement, there are individuals with malicious intent. By remaining vigilant and adopting necessary precautions, it is possible to outsmart hackers and safeguard personal information, maintaining your privacy and security.
Final Words on IoT in Cybersecurity
Unfortunately lack of security is still a major concern for many people and enterprises that look to adopt IoT technology. Recent DDoS and ransomware attacks have made some technology users even more cautious than they already were. Therefore, IoT Security is one of the key topics any organization will have to master in the coming years in order to comfortably roll-out their IoT-based solutions. However, developing IoT solutions that are secure from device to cloud and everything in between, is extremely complex. Just one weak link can be taken advantage of by attackers to access the network. Our research addresses this complexity and aims to help firms overcome the challenges of building secure IoT solutions in any industry.
Knud Lasse Lueth, MD at IoT Analytics